Difference between revisions of "Projects:2019s1-105 Hacking CAN Bus"
(→Method) |
|||
| (11 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | '''Utilising a | + | ''' Utilising a Vehicle Testbed Environment to Develop Deceptive CAN Bus Attacks''' |
| − | + | Welcome to the wiki page for the 2019 CAN Hacking Project by Stefan Smiljanic and Charlie Tran. Here you can track the progress of this honours project. Our project aims to develop and demonstrate the potency of targeted and deceptive CAN bus attacks in a vehicle testbed environment that was developed in 2018. | |
| − | + | == Introduction == | |
| − | The | + | :The controller area network (CAN) serial communications protocol has been widely used in the automotive industry for almost three decades. Within automotive vehicles, the CAN bus standard facilitates communication between all the electronic control units (ECUs) that manage a vehicle’s many functions. Access to the CAN by an adversary’s unauthenticated device allows it to listen, broadcast and intercept communications. |
| + | :Through message manipulation and injection, subtle and deceptive attacks capable of physical, social and financial damage can be developed to highlight the vulnerabilities of the CAN protocol. The victim’s dashboard could suggest that the vehicle requires servicing, is malfunctioning, or is travelling at a higher speed than displayed. This research will aim to develop and analyse these subtle and long-term attacks, rather than overtly disabling the engine or brakes. | ||
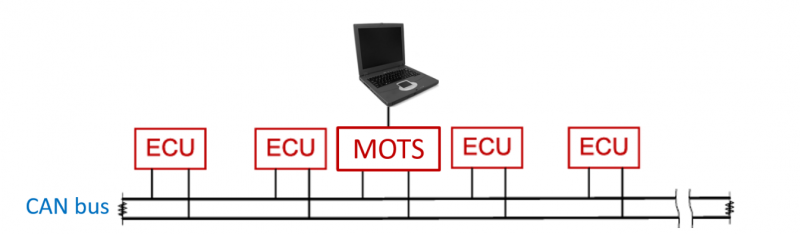
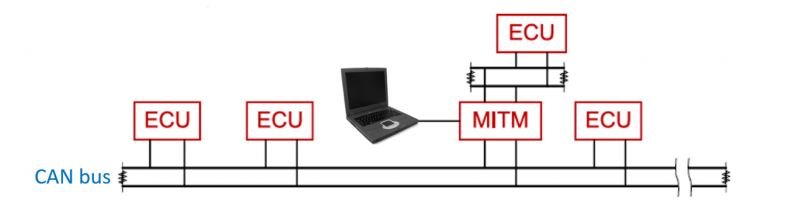
| − | + | :The attack architectures that will be considered are man-on-the-side (MOTS) and man-in-the-middle (MITM), where the attacking device is physically connected to the CAN bus. The MOTS architecture attaches the attacker’s device to the CAN bus directly to read and insert new messages on the network (see Figure 1). In MITM, the attacking device is inserted between an existing ECU and the CAN bus, allowing it to listen, broadcast and intercept messages (see Figure 2). | |
| − | + | ||
| − | + | ||
| + | [[File:MOTS.PNG|800px|'''Figure 1:''' Man-on-the-side attack architecture]] | ||
| + | |||
| + | '''Figure 1:''' Man-on-the-side attack architecture | ||
| + | |||
| + | [[File:MITM.PNG|800px|'''Figure 2:''' Man-in-the-middle attack architecture]] | ||
| + | |||
| + | '''Figure 2:''' Man-in-the-middle attack architecture | ||
| + | |||
| + | :The research presented in this paper will evaluate the effectiveness of subtle attacks as an undocumented cybersecurity threat for automotive CAN systems. These attacks will be developed in both MOTS and MITM architectures in a vehicle testbed environment. The research intends to highlight new threat scenarios and foster the development of new system solutions for automotive cybersecurity. | ||
| − | |||
| − | = | + | = Research Questions = |
| − | + | * What are the benefits and limitations of a testbed environment for research in automotive security? | |
| − | + | * How can the vulnerabilities of the CAN bus protocol be exploited in a testbed environment to perform targeted and deceptive attacks? | |
| − | + | * What are the advantages and disadvantages of MOTS compared to MITM attack architectures? | |
| − | |||
= Definitions and Abbreviations = | = Definitions and Abbreviations = | ||
| − | CAN | + | * '''CAN''' - Controller Area Network |
| + | |||
| + | * '''ECU''' - Electronic Control Unit | ||
| − | + | * '''MITM''' - Man-in-the-Middle | |
| − | + | * '''MOTS''' - Man-on-the-Side | |
| − | + | * '''OBD''' - On Board Diagnostics | |
| − | |||
| + | = Related Work and Motivation = | ||
| + | :The exploitation of CAN vulnerabilities is a well-researched field. Articles [1, 2] illustrate the ability to control the dashboard, engine and other systems in a MOTS architecture via the OBD-II port of a working vehicle. Some MOTS attacks can remotely access the CAN bus through Bluetooth and cellular radio [3]. Article [4] analysed the remote attack surface of a 2014 Jeep Cherokee, which demonstrated remote engine and brake control of the vehicle. This was possible due to a vulnerability that allowed malicious messages to be injected onto the vehicle’s CAN. | ||
| − | + | :Encryption and authentication protocols that would invalidate MOTS attacks and address the security flaws of existing vehicle CAN networks have been researched in the past [5, 6]. These protocols, however, impact the timing and safety robustness of the CAN standard and are not widely adopted by vehicle manufacturers [7]. | |
| − | |||
| − | + | :The MITM architecture was discussed in article [8], where a security auditing platform for OBD-II devices was created. Using its capability of blocking, forwarding and modifying CAN messages in real-time, the platform could be tested in an adversarial MITM attack between an ECU and the CAN bus. | |
| − | + | :Previous research has not sufficiently evaluated the impact of deceptive, targeted and subtle attacks on the vehicular CAN bus networks. This paper will address these concerns through threat modelling of both MOTS and MITM architectures in a testbed environment. | |
| − | |||
| − | |||
= Objectives = | = Objectives = | ||
| − | + | The research aims to: | |
| + | |||
| + | :*Discover and exploit CAN vulnerabilities to create attacks that are subtle and deceptive | ||
| + | |||
| + | :*Demonstrate and evaluate the attacks’ abilities to deceive or financially burden the victim | ||
| + | |||
| + | :*Implement these MITM and MOTS attack architectures on the testbed | ||
| + | |||
| + | :*Evaluate the vulnerabilities, threat scenarios and defence mechanisms | ||
| + | |||
| + | :*Highlight the usefulness of the testbed environment in developing CAN bus attacks | ||
| + | |||
| + | |||
| + | |||
| + | The extended objectives are to: | ||
| + | |||
| + | :*Create an attack framework for the implementation of the research on other vehicle models and manufacturers | ||
| + | |||
| + | :*Weaponise the attack in a small standalone hardware form factor | ||
| + | |||
| + | |||
= Method = | = Method = | ||
| − | + | The research objectives were achieved through the following method. | |
| + | |||
| + | :'''1.''' Identifying the CAN message IDs associated with a vehicle dashboard function by through a reverse engineering process of the the CAN bus message dumps collected from real-world data. | ||
| + | |||
| + | :'''2.''' Creating a systematic set of experiments to determine the most effective use of the CAN message in a deceptive attack. | ||
| + | |||
| + | :'''3.''' Implementing and demonstrating the attacks in both MOTS and MITM architectures in the testbed environment. | ||
| + | |||
| + | :'''4.''' Creating a device capable of executing all of the attacks by connecting: | ||
| + | |||
| + | ::'''a.''' To the OBD-II port for the MOTS architecture | ||
| − | = Results = | + | ::'''b.''' Between the dashboard and wiring loom for MITM architecture. |
| − | + | ||
| + | :'''5.''' Performing a threat analysis of the attacks and highlighting possible attack scenarios. | ||
| + | |||
| + | :'''6.''' Discussing the results and possible defence mechanisms. | ||
| + | |||
| + | = Final Results = | ||
| + | |||
| + | [[File:Figure Comparison Speedometer normal operation and operation while attacked.png|thumb|Comparison of speedometer normal operation and operation while attacked]] | ||
| + | |||
| + | :The testbed used in this research was created by former honours students of the University of Adelaide in 2018 and consists of four main ECUs and a dashboard from a 2016 Mazda2 [9]. By playing back real CAN data onto the testbed, gathered from logging CAN communications while driving, the CAN message ID that related to the dashboard’s odometer reading was identified. This is an undocumented finding that was used to develop a targeted MOTS attack by increasing the odometer. | ||
| + | |||
| + | :The odometer attack developed used this CAN ID by maliciously injecting specific CAN messages to increase the odometer excessively while driving. This attack was implemented in both MOTS and MITM attack architectures. | ||
| + | |||
| + | :Development of the attacks was completed in python using the phyton-can API to perform real-time message handling of CAN data. The result was incorporation of the speedometer and odometer dashboard attacks in both architectures. The results were verified using realistic driving simulation environments by applying two CAN devices: one to transmit simulated driving messages and the other to read and send malicious messages. | ||
| + | |||
| + | :The attack demonstrated in the figure below shows the simulated vehicle driving at 50km/hr. The top photograph is during normal playback conditions of the CAN log file. The bottom photograph is during the speedometer attack execution. Attack execution refers to the same playback conditions, except that another CAN transceiver is executing SpeedoBias_MOTS.py attack code. | ||
| + | |||
| + | |||
| + | :In depth threat analysis is discussed in the research an concludes the potential for serious financial damage capabilities of the attacks. The results verify the vulnerabilities in CAN and implement serveral unique subtle, deceptive and damaging attacks in two different attack architectures. A conclusion is drawn to the strengths of the MOTS attack implementations over MITM. | ||
= References = | = References = | ||
| − | + | :'''[1]''' K. Koscher, A. Czeskis, F. Roesner, S. Patel, T. Kohno, S. Checkoway, D. McCoy, B. Kantor, D. Anderson, H. Shacham, and S. Savage, “Experimental security analysis of a modern automobile“, 2010 IEEE Symposium on Security and Privacy, 2010, pp. 447–462. | |
| + | |||
| + | :'''[2]''' R. Currie, “Hacking the CAN Bus: Basic Manipulation of a Modern Automobile Through CAN Bus Reverse Engineering”, 2017, [Online]. Available: https://www.sans.org/reading-room/whitepapers/threats/paper/37825 | ||
| + | |||
| + | :'''[3]''' S. Checkoway, D. McCoy, B. Kantor, D. Anderson, H. Shacham, S. Savage, K. Koscher, A. Czeskis, F. Roesner, T. Kohno, “Comprehensive experimental analyses of automotive attack surfaces,” Proceedings of the 20th USENIX Conference on Security, ser. SEC’11. Berkeley, CA, USA: USENIX Association, 2011, pp. 6-6. | ||
| + | |||
| + | :'''[4]''' C. Miller and C. Valasek, “Remote Exploitation of an Unaltered Passenger Vehicle”, 2015, [Online]. Available: http://illmatics.com/Remote%20Car%20Hacking.pdf | ||
| + | |||
| + | :'''[5]''' A. Hazem and H.A.H. Fahmy, “LCAP - A Lightweight CAN Authentication Protocol for Securing In-Vehicle Networks”, 2012, [Online]. Available: http://eece.cu.edu.eg/~hfahmy/publish/escar2012.pdf | ||
| + | |||
| + | :'''[6]''' A.I. Radu and F.D. Garcia, “LeiA: A Lightweight Authentication Protocol for CAN”, in Proc. Int. Conf. Eur. Symp. Res. Comput. Security, 2016, pp. 283–300. | ||
| + | |||
| + | :'''[7]''' B. Boldt, “Automotive Security in a CAN”, 2017, [Online]. Available: https://www.electronicdesign.com/automotive/automotive-security-can | ||
| + | |||
| + | :'''[8]''' A. Lebrun and J.C. Demay, “CANSPY: a Platform for Auditing CAN Devices”, 2017, [Online]. Available: https://www.blackhat.com/docs/us-16/materials/us-16-Demay-CANSPY-A-Platorm-For-Auditing-CAN-Devices-wp.pdf | ||
| + | |||
| + | :'''[9]''' L. Oliveira, M. Pfeiffer, T. Taziva, A. Frishling, B. Cooney, D. Coscia and M. Sorell, “The challenges of building a testbed environment for security and vulnerability analysis of internal communication networks in vehicles,” 4th Interdisciplinary Cyber Research Workshop, 2018. | ||
| + | |||
| + | |||
| + | |||
| + | |||
| + | |||
| + | = Project Team = | ||
| + | == Student Researchers == | ||
| + | Stefan Smiljanic | ||
| + | |||
| + | Charlie Tran | ||
| + | |||
| + | == Project Supervisors == | ||
| + | Dr. Matthew Sorell | ||
| + | |||
| + | Aaron Frishling (DSTG) | ||
| + | |||
| + | Bradley Cooney (DSTG) | ||
| + | |||
| + | Daniel Coscia (DSTG) | ||
Latest revision as of 04:32, 30 October 2019
Utilising a Vehicle Testbed Environment to Develop Deceptive CAN Bus Attacks
Welcome to the wiki page for the 2019 CAN Hacking Project by Stefan Smiljanic and Charlie Tran. Here you can track the progress of this honours project. Our project aims to develop and demonstrate the potency of targeted and deceptive CAN bus attacks in a vehicle testbed environment that was developed in 2018.
Contents
Introduction
- The controller area network (CAN) serial communications protocol has been widely used in the automotive industry for almost three decades. Within automotive vehicles, the CAN bus standard facilitates communication between all the electronic control units (ECUs) that manage a vehicle’s many functions. Access to the CAN by an adversary’s unauthenticated device allows it to listen, broadcast and intercept communications.
- Through message manipulation and injection, subtle and deceptive attacks capable of physical, social and financial damage can be developed to highlight the vulnerabilities of the CAN protocol. The victim’s dashboard could suggest that the vehicle requires servicing, is malfunctioning, or is travelling at a higher speed than displayed. This research will aim to develop and analyse these subtle and long-term attacks, rather than overtly disabling the engine or brakes.
- The attack architectures that will be considered are man-on-the-side (MOTS) and man-in-the-middle (MITM), where the attacking device is physically connected to the CAN bus. The MOTS architecture attaches the attacker’s device to the CAN bus directly to read and insert new messages on the network (see Figure 1). In MITM, the attacking device is inserted between an existing ECU and the CAN bus, allowing it to listen, broadcast and intercept messages (see Figure 2).
Figure 1: Man-on-the-side attack architecture
Figure 2: Man-in-the-middle attack architecture
- The research presented in this paper will evaluate the effectiveness of subtle attacks as an undocumented cybersecurity threat for automotive CAN systems. These attacks will be developed in both MOTS and MITM architectures in a vehicle testbed environment. The research intends to highlight new threat scenarios and foster the development of new system solutions for automotive cybersecurity.
Research Questions
- What are the benefits and limitations of a testbed environment for research in automotive security?
- How can the vulnerabilities of the CAN bus protocol be exploited in a testbed environment to perform targeted and deceptive attacks?
- What are the advantages and disadvantages of MOTS compared to MITM attack architectures?
Definitions and Abbreviations
- CAN - Controller Area Network
- ECU - Electronic Control Unit
- MITM - Man-in-the-Middle
- MOTS - Man-on-the-Side
- OBD - On Board Diagnostics
Related Work and Motivation
- The exploitation of CAN vulnerabilities is a well-researched field. Articles [1, 2] illustrate the ability to control the dashboard, engine and other systems in a MOTS architecture via the OBD-II port of a working vehicle. Some MOTS attacks can remotely access the CAN bus through Bluetooth and cellular radio [3]. Article [4] analysed the remote attack surface of a 2014 Jeep Cherokee, which demonstrated remote engine and brake control of the vehicle. This was possible due to a vulnerability that allowed malicious messages to be injected onto the vehicle’s CAN.
- Encryption and authentication protocols that would invalidate MOTS attacks and address the security flaws of existing vehicle CAN networks have been researched in the past [5, 6]. These protocols, however, impact the timing and safety robustness of the CAN standard and are not widely adopted by vehicle manufacturers [7].
- The MITM architecture was discussed in article [8], where a security auditing platform for OBD-II devices was created. Using its capability of blocking, forwarding and modifying CAN messages in real-time, the platform could be tested in an adversarial MITM attack between an ECU and the CAN bus.
- Previous research has not sufficiently evaluated the impact of deceptive, targeted and subtle attacks on the vehicular CAN bus networks. This paper will address these concerns through threat modelling of both MOTS and MITM architectures in a testbed environment.
Objectives
The research aims to:
- Discover and exploit CAN vulnerabilities to create attacks that are subtle and deceptive
- Demonstrate and evaluate the attacks’ abilities to deceive or financially burden the victim
- Implement these MITM and MOTS attack architectures on the testbed
- Evaluate the vulnerabilities, threat scenarios and defence mechanisms
- Highlight the usefulness of the testbed environment in developing CAN bus attacks
The extended objectives are to:
- Create an attack framework for the implementation of the research on other vehicle models and manufacturers
- Weaponise the attack in a small standalone hardware form factor
Method
The research objectives were achieved through the following method.
- 1. Identifying the CAN message IDs associated with a vehicle dashboard function by through a reverse engineering process of the the CAN bus message dumps collected from real-world data.
- 2. Creating a systematic set of experiments to determine the most effective use of the CAN message in a deceptive attack.
- 3. Implementing and demonstrating the attacks in both MOTS and MITM architectures in the testbed environment.
- 4. Creating a device capable of executing all of the attacks by connecting:
- a. To the OBD-II port for the MOTS architecture
- b. Between the dashboard and wiring loom for MITM architecture.
- 5. Performing a threat analysis of the attacks and highlighting possible attack scenarios.
- 6. Discussing the results and possible defence mechanisms.
Final Results
- The testbed used in this research was created by former honours students of the University of Adelaide in 2018 and consists of four main ECUs and a dashboard from a 2016 Mazda2 [9]. By playing back real CAN data onto the testbed, gathered from logging CAN communications while driving, the CAN message ID that related to the dashboard’s odometer reading was identified. This is an undocumented finding that was used to develop a targeted MOTS attack by increasing the odometer.
- The odometer attack developed used this CAN ID by maliciously injecting specific CAN messages to increase the odometer excessively while driving. This attack was implemented in both MOTS and MITM attack architectures.
- Development of the attacks was completed in python using the phyton-can API to perform real-time message handling of CAN data. The result was incorporation of the speedometer and odometer dashboard attacks in both architectures. The results were verified using realistic driving simulation environments by applying two CAN devices: one to transmit simulated driving messages and the other to read and send malicious messages.
- The attack demonstrated in the figure below shows the simulated vehicle driving at 50km/hr. The top photograph is during normal playback conditions of the CAN log file. The bottom photograph is during the speedometer attack execution. Attack execution refers to the same playback conditions, except that another CAN transceiver is executing SpeedoBias_MOTS.py attack code.
- In depth threat analysis is discussed in the research an concludes the potential for serious financial damage capabilities of the attacks. The results verify the vulnerabilities in CAN and implement serveral unique subtle, deceptive and damaging attacks in two different attack architectures. A conclusion is drawn to the strengths of the MOTS attack implementations over MITM.
References
- [1] K. Koscher, A. Czeskis, F. Roesner, S. Patel, T. Kohno, S. Checkoway, D. McCoy, B. Kantor, D. Anderson, H. Shacham, and S. Savage, “Experimental security analysis of a modern automobile“, 2010 IEEE Symposium on Security and Privacy, 2010, pp. 447–462.
- [2] R. Currie, “Hacking the CAN Bus: Basic Manipulation of a Modern Automobile Through CAN Bus Reverse Engineering”, 2017, [Online]. Available: https://www.sans.org/reading-room/whitepapers/threats/paper/37825
- [3] S. Checkoway, D. McCoy, B. Kantor, D. Anderson, H. Shacham, S. Savage, K. Koscher, A. Czeskis, F. Roesner, T. Kohno, “Comprehensive experimental analyses of automotive attack surfaces,” Proceedings of the 20th USENIX Conference on Security, ser. SEC’11. Berkeley, CA, USA: USENIX Association, 2011, pp. 6-6.
- [4] C. Miller and C. Valasek, “Remote Exploitation of an Unaltered Passenger Vehicle”, 2015, [Online]. Available: http://illmatics.com/Remote%20Car%20Hacking.pdf
- [5] A. Hazem and H.A.H. Fahmy, “LCAP - A Lightweight CAN Authentication Protocol for Securing In-Vehicle Networks”, 2012, [Online]. Available: http://eece.cu.edu.eg/~hfahmy/publish/escar2012.pdf
- [6] A.I. Radu and F.D. Garcia, “LeiA: A Lightweight Authentication Protocol for CAN”, in Proc. Int. Conf. Eur. Symp. Res. Comput. Security, 2016, pp. 283–300.
- [7] B. Boldt, “Automotive Security in a CAN”, 2017, [Online]. Available: https://www.electronicdesign.com/automotive/automotive-security-can
- [8] A. Lebrun and J.C. Demay, “CANSPY: a Platform for Auditing CAN Devices”, 2017, [Online]. Available: https://www.blackhat.com/docs/us-16/materials/us-16-Demay-CANSPY-A-Platorm-For-Auditing-CAN-Devices-wp.pdf
- [9] L. Oliveira, M. Pfeiffer, T. Taziva, A. Frishling, B. Cooney, D. Coscia and M. Sorell, “The challenges of building a testbed environment for security and vulnerability analysis of internal communication networks in vehicles,” 4th Interdisciplinary Cyber Research Workshop, 2018.
Project Team
Student Researchers
Stefan Smiljanic
Charlie Tran
Project Supervisors
Dr. Matthew Sorell
Aaron Frishling (DSTG)
Bradley Cooney (DSTG)
Daniel Coscia (DSTG)