Difference between revisions of "Projects:2017s1-167b Real Time Video Steam Substitution"
(→Point of substitution) |
|||
| (6 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| + | == Project Members == | ||
| + | |||
| + | • Matt Reynolds | ||
| + | |||
| + | • Harish Gowda | ||
| + | |||
| + | == Project Supervisor == | ||
| + | |||
| + | • Dr. Matthew Sorell | ||
| + | |||
== Introduction == | == Introduction == | ||
NATO’s Locked Shields [1] is an annual (since 2010) live-fire cyber defence exercise organised to aid in the training of security experts tasked with protecting national IT systems. The scenario-based exercise focuses on the attack and defence of network and service infrastructure of a fictional country, including military command and control systems, electrical power grid systems and unmanned aerial vehicles. One such attack performed at the 2017 event focused on the substitution of footage from a military drone’s real-time video feed. The defence network was compromised with the video feed replaced and displayed on screen. This was achieved via the use of VLC command line options. | NATO’s Locked Shields [1] is an annual (since 2010) live-fire cyber defence exercise organised to aid in the training of security experts tasked with protecting national IT systems. The scenario-based exercise focuses on the attack and defence of network and service infrastructure of a fictional country, including military command and control systems, electrical power grid systems and unmanned aerial vehicles. One such attack performed at the 2017 event focused on the substitution of footage from a military drone’s real-time video feed. The defence network was compromised with the video feed replaced and displayed on screen. This was achieved via the use of VLC command line options. | ||
Taking inspiration from the recently concluded event and the attack performed on the drone, this project investigates how a real-time video stream can be seamlessly substituted whilst going undetected. Consequently, the investigation will generate the need for further research into uncovered vulnerabilities and their potential solutions. | Taking inspiration from the recently concluded event and the attack performed on the drone, this project investigates how a real-time video stream can be seamlessly substituted whilst going undetected. Consequently, the investigation will generate the need for further research into uncovered vulnerabilities and their potential solutions. | ||
| − | == | + | == Estonia Study Tour == |
| + | As part of this research project, we had the privilege of attending a 2-week study tour in Estonia. Participation gave us the opportunity to witness firsthand the progress Estonia is making in the world of cyber security. We found it to be an invaluable experience as it allowed us to network with fellow peers and professionals. | ||
| + | |||
| + | == Project Aim == | ||
This research project looks at how intercepting and substituting the contents of a real-time video stream between a source and end-user over IP may be conducted. The real-time video stream is to be seamlessly substituted with an arbitrary video or an alternate stream. The project aims to identify all the complexities and constraints associated with conducting such a substitution. | This research project looks at how intercepting and substituting the contents of a real-time video stream between a source and end-user over IP may be conducted. The real-time video stream is to be seamlessly substituted with an arbitrary video or an alternate stream. The project aims to identify all the complexities and constraints associated with conducting such a substitution. | ||
| + | |||
The project is divided into two components: | The project is divided into two components: | ||
| − | + | * Multimedia Network Security and | |
| − | + | * Video stream Substitution | |
| − | The Multimedia Network Security aspect of the project considers different attack strategies which can be implemented to gain access to the real-time stream. This is while also keeping the end users unaware of any breaches in the network. Different session hijacking techniques and their complexities are to be examined. As a starting point, it is assumed network encryption is omitted. | + | The Multimedia Network Security aspect of the project considers different attack strategies which can be implemented to gain access to the real-time stream. This is while also keeping the end users unaware of any breaches in the network. Different session hijacking techniques and their complexities are to be examined. As a starting point, it is assumed network encryption is omitted. |
| + | The Video substitution component of the project considers the associated challenges of manipulating and seamlessly substituting a video stream in real-time. Motion JPEG and MPEG standards 2 and 4 are of focus. | ||
| − | == | + | == Objectives == |
| + | |||
| + | == Concept == | ||
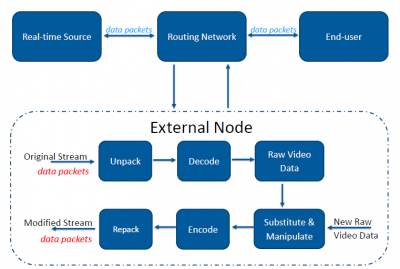
| + | Consider the following high-level concept where a real-time stream originates from some source, is sent through a routing network over IP and arrives at the end-user. A man-in-the-middle attack can be performed at a vulnerable point within the routing network to hijack the connection. From here all data can then be routed through an external node for manipulation. | ||
| + | |||
| + | |||
| + | [[File:Highlevel.PNG|center|400px]] | ||
| + | |||
| + | |||
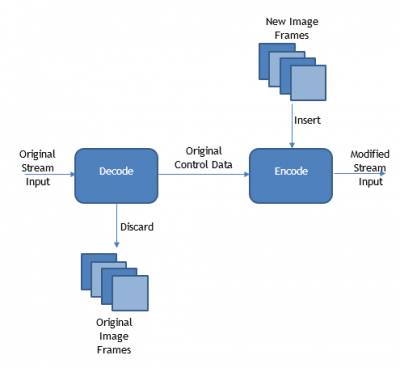
| + | At the external node, the objective is to pull apart and break down the video stream into its elementary components. Relevant stream control data including timestamps, clock references and frame rate information are to be extracted and retained, with the video frames discarded. The stream can then be re-encoded using the retained stream control data and new video frames. | ||
| + | |||
| + | |||
| + | [[File:Highlevel2.PNG|center|400px]] | ||
| + | |||
| + | == Technical Challenges == | ||
| + | |||
| + | === Maintain real-time stream characteristics === | ||
| + | As with any transmission of data, there is an inherent delay introduced into the system. Delay is introduced not only during transmission, but also when the end-user receives, decodes and displays the video. Any additional delay introduced to the system as part of the substitution process must be capped at a reasonable limit to ensure the stream remains real-time. Any significant delay caused from this process will breach the requirement for the stream to exhibit a seamless transition. | ||
| + | |||
| + | === Seamless substitution === | ||
| + | A key requirement is that the substitution of the video stream is to be seamless. This itself presents many challenges and has many variables. A truly seamless substitution may not be achievable. | ||
| + | |||
| + | === Packet alteration === | ||
| + | After packet manipulation, there will be an alteration to the size of the packet payload. This can be attributed to many things: | ||
| + | * Frame size/Resolution – there may be a discrepancy between the size of the original frame and its replacement, i.e., replacing a 1280x720 pixel frame with a 1920x1080 pixel frame. | ||
| + | * Frame rate – within each packet there is the possibility of a varying number of frames. Evidently if the number of frames within the packet is altered, there will be an effect on the packet size. | ||
| + | These factors can be addressed however could limit functionality. | ||
| + | |||
| + | |||
| + | === Point of substitution === | ||
| + | It's not always feasible to pick a precise arbitrary point of substitution, dependant on the video compression scheme used at the encoder. | ||
| + | |||
| + | === Synchronisation and control information === | ||
| + | It is imperative that clock reference data and timestamps from the stream are preserved. | ||
| + | The ISO/IEC 13813-1 standard requires that at the time of encoding, the PTS is to be encoded not less than every 700ms. Although not required to be encoded within every PES packet, it is however common. | ||
| + | Preserving and ‘grafting’ these timestamps onto the new video data is the greatest challenge that needs to be addressed. | ||
| − | |||
| − | + | == Future Work == | |
| + | === Address network security === | ||
| + | As a first step, we’ve considered a theoretical attack on a network with no data encryption and security. In practice, this isn’t all that feasible. The next step would be to investigate the vulnerabilities and potential for exploits in a secured network. | ||
| − | == | + | === Tool Development === |
| + | Based on the research conducted, there’s the possibility to develop a tool capable of real-time video stream substitution. FFMPEG is an open source tool capable video/stream editing and would serve as an ideal platform. | ||
| − | + | == References == | |
| + | [1] “Locked Shields 2017,” NATO Cooperative Cyber Defence Centre of Excellence, 2017. [Online]. Available: https://ccdcoe.org/locked-shields-2017.html. | ||
Latest revision as of 11:10, 30 October 2017
Contents
Project Members
• Matt Reynolds
• Harish Gowda
Project Supervisor
• Dr. Matthew Sorell
Introduction
NATO’s Locked Shields [1] is an annual (since 2010) live-fire cyber defence exercise organised to aid in the training of security experts tasked with protecting national IT systems. The scenario-based exercise focuses on the attack and defence of network and service infrastructure of a fictional country, including military command and control systems, electrical power grid systems and unmanned aerial vehicles. One such attack performed at the 2017 event focused on the substitution of footage from a military drone’s real-time video feed. The defence network was compromised with the video feed replaced and displayed on screen. This was achieved via the use of VLC command line options. Taking inspiration from the recently concluded event and the attack performed on the drone, this project investigates how a real-time video stream can be seamlessly substituted whilst going undetected. Consequently, the investigation will generate the need for further research into uncovered vulnerabilities and their potential solutions.
Estonia Study Tour
As part of this research project, we had the privilege of attending a 2-week study tour in Estonia. Participation gave us the opportunity to witness firsthand the progress Estonia is making in the world of cyber security. We found it to be an invaluable experience as it allowed us to network with fellow peers and professionals.
Project Aim
This research project looks at how intercepting and substituting the contents of a real-time video stream between a source and end-user over IP may be conducted. The real-time video stream is to be seamlessly substituted with an arbitrary video or an alternate stream. The project aims to identify all the complexities and constraints associated with conducting such a substitution.
The project is divided into two components:
- Multimedia Network Security and
- Video stream Substitution
The Multimedia Network Security aspect of the project considers different attack strategies which can be implemented to gain access to the real-time stream. This is while also keeping the end users unaware of any breaches in the network. Different session hijacking techniques and their complexities are to be examined. As a starting point, it is assumed network encryption is omitted.
The Video substitution component of the project considers the associated challenges of manipulating and seamlessly substituting a video stream in real-time. Motion JPEG and MPEG standards 2 and 4 are of focus.
Objectives
Concept
Consider the following high-level concept where a real-time stream originates from some source, is sent through a routing network over IP and arrives at the end-user. A man-in-the-middle attack can be performed at a vulnerable point within the routing network to hijack the connection. From here all data can then be routed through an external node for manipulation.
At the external node, the objective is to pull apart and break down the video stream into its elementary components. Relevant stream control data including timestamps, clock references and frame rate information are to be extracted and retained, with the video frames discarded. The stream can then be re-encoded using the retained stream control data and new video frames.
Technical Challenges
Maintain real-time stream characteristics
As with any transmission of data, there is an inherent delay introduced into the system. Delay is introduced not only during transmission, but also when the end-user receives, decodes and displays the video. Any additional delay introduced to the system as part of the substitution process must be capped at a reasonable limit to ensure the stream remains real-time. Any significant delay caused from this process will breach the requirement for the stream to exhibit a seamless transition.
Seamless substitution
A key requirement is that the substitution of the video stream is to be seamless. This itself presents many challenges and has many variables. A truly seamless substitution may not be achievable.
Packet alteration
After packet manipulation, there will be an alteration to the size of the packet payload. This can be attributed to many things:
- Frame size/Resolution – there may be a discrepancy between the size of the original frame and its replacement, i.e., replacing a 1280x720 pixel frame with a 1920x1080 pixel frame.
- Frame rate – within each packet there is the possibility of a varying number of frames. Evidently if the number of frames within the packet is altered, there will be an effect on the packet size.
These factors can be addressed however could limit functionality.
Point of substitution
It's not always feasible to pick a precise arbitrary point of substitution, dependant on the video compression scheme used at the encoder.
Synchronisation and control information
It is imperative that clock reference data and timestamps from the stream are preserved. The ISO/IEC 13813-1 standard requires that at the time of encoding, the PTS is to be encoded not less than every 700ms. Although not required to be encoded within every PES packet, it is however common. Preserving and ‘grafting’ these timestamps onto the new video data is the greatest challenge that needs to be addressed.
Future Work
Address network security
As a first step, we’ve considered a theoretical attack on a network with no data encryption and security. In practice, this isn’t all that feasible. The next step would be to investigate the vulnerabilities and potential for exploits in a secured network.
Tool Development
Based on the research conducted, there’s the possibility to develop a tool capable of real-time video stream substitution. FFMPEG is an open source tool capable video/stream editing and would serve as an ideal platform.
References
[1] “Locked Shields 2017,” NATO Cooperative Cyber Defence Centre of Excellence, 2017. [Online]. Available: https://ccdcoe.org/locked-shields-2017.html.